Description
The complete ethical hacking course: beginner to advanced equips employees with the skills to identify and mitigate cybersecurity threats. By the end of this course, participants will have enhanced abilities to analyze security breaches, apply ethical hacking practices, and strengthen organizational defenses. The course’s structured approach, featuring introductions, in-depth explorations, real-world scenarios, and summaries, ensures comprehensive learning.
Participants will engage in interactive simulations and case studies, gaining hands-on experience in detecting and countering threats. By integrating these practical exercises, the course ensures that learners can apply their knowledge in real-world situations, improving their problem-solving and decision-making capabilities. Additionally, the course is fully customizable and scalable, allowing organizations to tailor content to their specific needs.
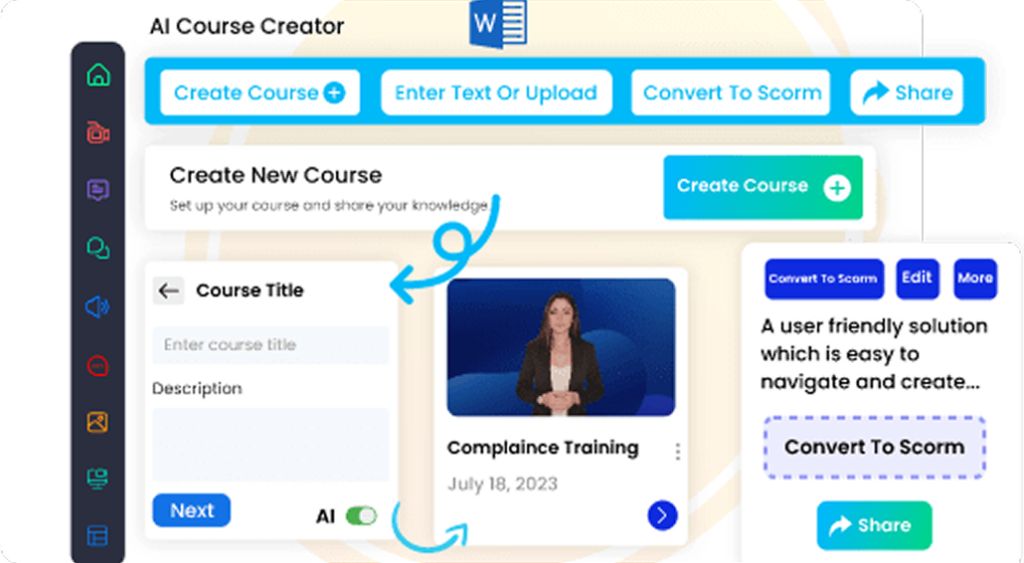
Employees who complete this training will be better prepared to protect their organizations from cyber threats, resulting in improved security protocols and reduced risks. The continuous development features of the course, created using the CogniSpark AI-powered eLearning authoring tool, provide a dynamic learning environment that evolves with industry trends. This fully editable SCORM Course can be seamlessly integrated into any LMS, ensuring a smooth learning experience.
Who Is This Course For?
- IT Managers seeking comprehensive Ethical Hacking Training for Employees to fortify organizational cybersecurity.
- Cybersecurity professionals looking for an Online Ethical Hacking Course to enhance their skills and knowledge base.
- Network administrators aiming to improve their understanding of network vulnerabilities through advanced training.
- L&D Managers interested in integrating Ethical Hacking Training for Employees into corporate training programs.
Reasons to Choose Our eLearning Course Catalog
Editable & Embeddable SCORM Course
Easily modify the course content and structure to suit your
needs, then embed it directly into any SCORM-compliant LMS
for seamless deployment and tracking.
Fully Customizable with Built-In Authoring Tools
Adapt course content, visuals, and structure to meet your
specific learning objectives with ease.
White Label eLearning Courses
Seamlessly integrate your branding and deliver a consistent
learning experience across your organization.
Engaging Content Through Storytelling and Scenarios
Increase retention with real-world communication challenges,
story-driven modules, and practical examples.
Interactive Learning Using Animation and Gamification
Drive learner engagement with visually rich animations, simulations, and game-based learning strategies.
Flexible, Budget-Friendly Pricing Options
Choose a pricing model that fits your organizational needs, whether you’re a startup or a large enterprise.
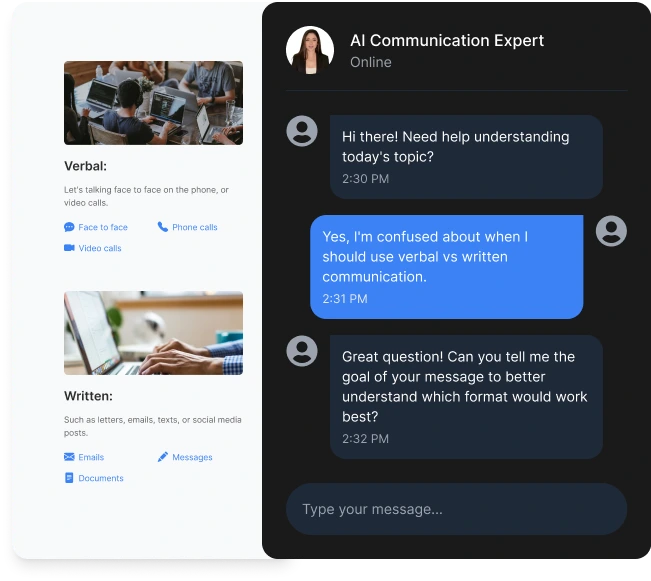
How AI Tutor Helps in eLearning Courses?
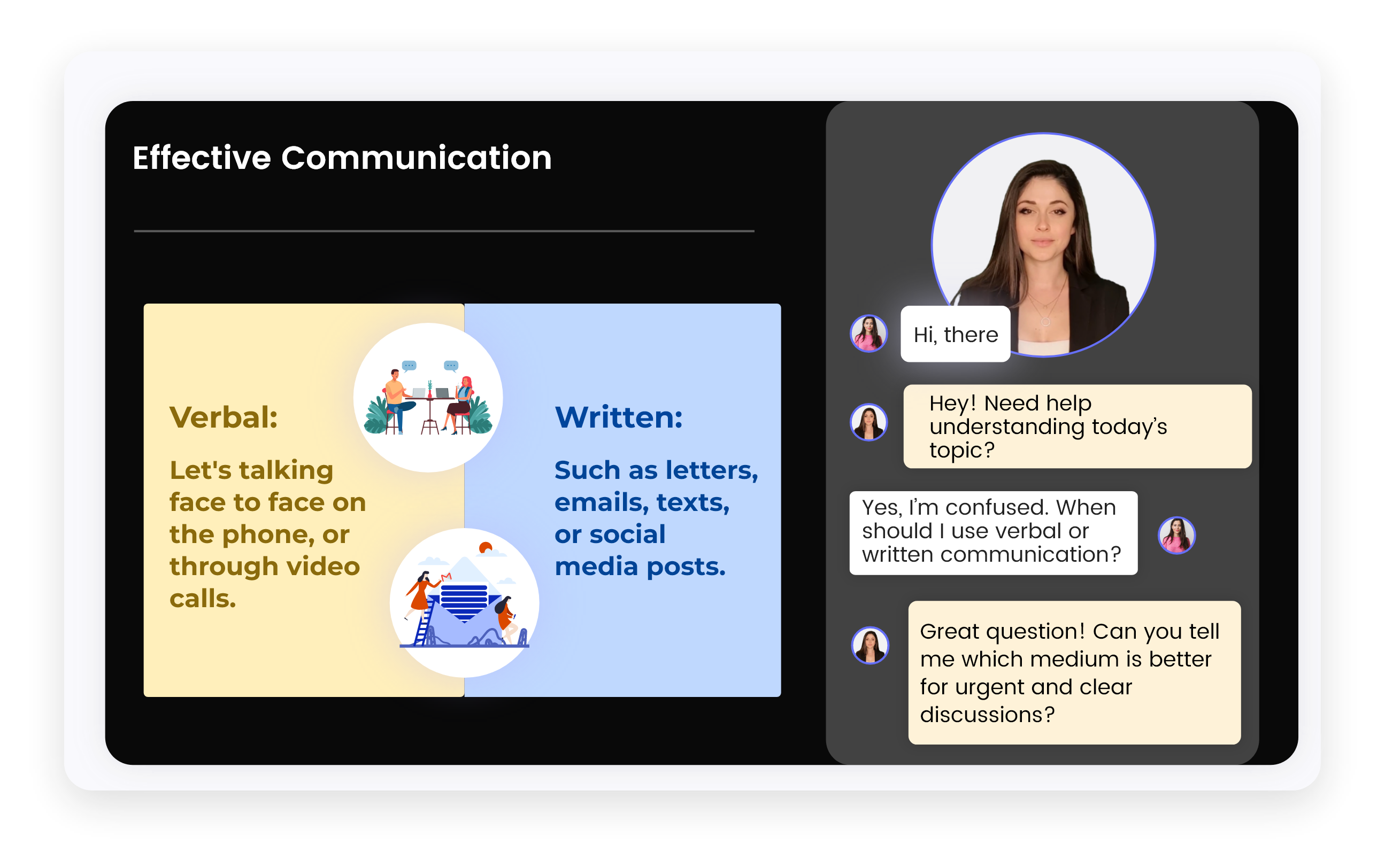
Guides learners through the eLearning course
with a personalized, step-by-step learning path.
Explains complex topics in real-time using simple,
easy-to-understand multiple language.
Offers quizzes, helpful hints, and feedback to enhance
understanding and track progress.
Supports voice interaction, allowing learners to speak
instead of type and receive responses in audio format for
a hands-free, engaging experience.
Simulates real-world scenarios through role plays and
interactive simulations to build practical skills and boost
confidence
FAQs (Frequently Asked Questions)
+
The objectives include equipping employees with skills to identify cybersecurity threats and apply ethical hacking practices, offering comprehensive training online.
+
It offers a structured learning approach, interactive elements, hands-on practice, and full customizability, making it ideal for corporate environments.
+
Benefits include enhanced cybersecurity skills, improved problem-solving abilities, and the option to integrate training into existing LMS systems.
+
No prerequisites required, making it accessible to beginners and advanced learners alike, suitable for corporate employees seeking comprehensive training.
+
Yes, the course is fully customizable and scalable, allowing organizations to tailor content to meet specific departmental requirements and integrate into their LMS.