Why Information Security Training is Crucial
Cybersecurity threats are becoming increasingly sophisticated, and the human element often remains the weakest link in an organization’s defense. According to the 2024 Cybersecurity Workforce Study, human error is responsible for a significant portion of data breaches. From clicking phishing links to using weak passwords, employees can unintentionally create vulnerabilities in a company’s security posture. That’s where security awareness training comes in.
Information security training educates employees on best practices for handling sensitive data, recognizing security threats, and applying security protocols effectively. When employees understand the importance of security and how to protect the organization, they can reduce the risk of data breaches, minimize vulnerabilities, and improve overall digital hygiene.
Key Elements of Information Security Training
Effective information security training covers a range of topics, from identifying common security threats to applying company-specific security measures. Below are the key elements that should be included in any comprehensive employee training program:
1. Recognizing Phishing and Social Engineering Attacks
Phishing remains one of the most common methods cybercriminals use to exploit businesses. Employees need to understand how to spot phishing emails, fraudulent websites, and other social engineering tactics. Security awareness training should provide real-world examples and case studies to help employees identify and report phishing attempts.
2. Strong Password Policies and Authentication Practices
Weak passwords are an open invitation for cybercriminals. Employees must be trained to create strong, unique passwords and encouraged to use multi-factor authentication (MFA) whenever possible. Emphasizing the importance of password managers and the dangers of password reuse can significantly reduce the risk of credential theft.
3. Data Encryption and Secure Communication
Encryption is one of the most effective ways to protect data in transit. Employees should be familiar with the importance of encrypting sensitive files and using secure communication channels, whether they are sending emails or sharing files.
4. Safe Browsing and Internet Usage
Employees should be trained to recognize the risks of browsing unsecured websites, downloading files from untrusted sources, and engaging with online content that could put the company at risk. This training should also cover the dangers of using public Wi-Fi networks and the importance of VPNs for secure connections.
5. Handling and Storing Sensitive Data
Proper data handling and storage are critical components of information security. Employees must understand the organization’s policies around data storage, access permissions, and how to securely delete sensitive files.
6. Incident Reporting and Response
Even with the best training, security incidents can still happen. Employees should know how to report suspicious activity, identify potential breaches, and follow established procedures to mitigate damage. Quick reporting and response can make a significant difference in preventing widespread damage.
Learning Built Around Your Goals.
Discover how our courses can align with your training goals and drive real results.
Best Practices for Delivering Information Security Training
Information security training is only effective if it is delivered in a way that engages employees and reinforces good habits. Here are some best practices to ensure your training program succeeds:
1. Use Interactive and Engaging Content
People learn best when they actively engage with content. Incorporating quizzes, simulations, and interactive modules can help reinforce key concepts and keep employees engaged throughout the training.
2. Tailor Training to Different Roles
While all employees should receive basic security training, certain roles may require more specialized knowledge. For instance, IT staff may need advanced training on network security, while HR professionals may need more insight into protecting employee data. Customizing the training based on job functions ensures relevance and effectiveness.
3. Provide Ongoing Training and Refresher Courses
Cybersecurity is constantly evolving, and so should your training. Offering ongoing training and refresher courses keeps employees updated on the latest threats, security technologies, and company policies. This approach ensures that security awareness remains top of mind.
4. Incorporate Real-World Scenarios
Use real-world examples of data breaches and security incidents to demonstrate the potential consequences of neglecting information security. Seeing the impact of security breaches can help employees understand the gravity of their actions and the importance of following security protocols.
5. Gamify the Learning Experience
Gamification can be a great way to make security training fun and engaging. Implementing leaderboards, badges, and rewards for completing challenges or successfully identifying threats can motivate employees to stay focused and committed to their training.
Why Choose Information Security Training for Employees?
When implemented properly, information security training for employees can offer a multitude of benefits to an organization:
- Reduced Risk of Data Breaches: Employees trained to recognize threats are less likely to fall victim to phishing attacks or other forms of social engineering.
- Increased Cyber Hygiene: A culture of cybersecurity awareness leads to better practices, such as strong passwords, data encryption, and secure communication.
- Compliance with Regulations: Many industries have specific regulatory requirements for cybersecurity training. Regular training ensures compliance with standards such as GDPR, HIPAA, and PCI DSS.
- Improved Incident Response: When employees are trained to report security issues promptly, the organization can react faster to potential threats and minimize damage.
- Stronger Company Reputation: Organizations known for protecting their digital assets build trust with customers, clients, and partners.
How CogniSpark AI Elevates Information Security Training for Employees
In a world where cyber threats are increasingly sophisticated, CogniSpark AI provides a powerful, adaptive solution for Information Security Training—equipping your workforce with the knowledge and vigilance needed to protect your digital infrastructure.
With the help of AI-powered microlearning and scenario-based simulations, CogniSpark delivers engaging training experiences that help employees identify phishing attempts, manage passwords securely, and follow safe data handling practices. Its real-time AI Tutor offers personalized feedback, reinforcing key security protocols and promoting responsible digital behavior.
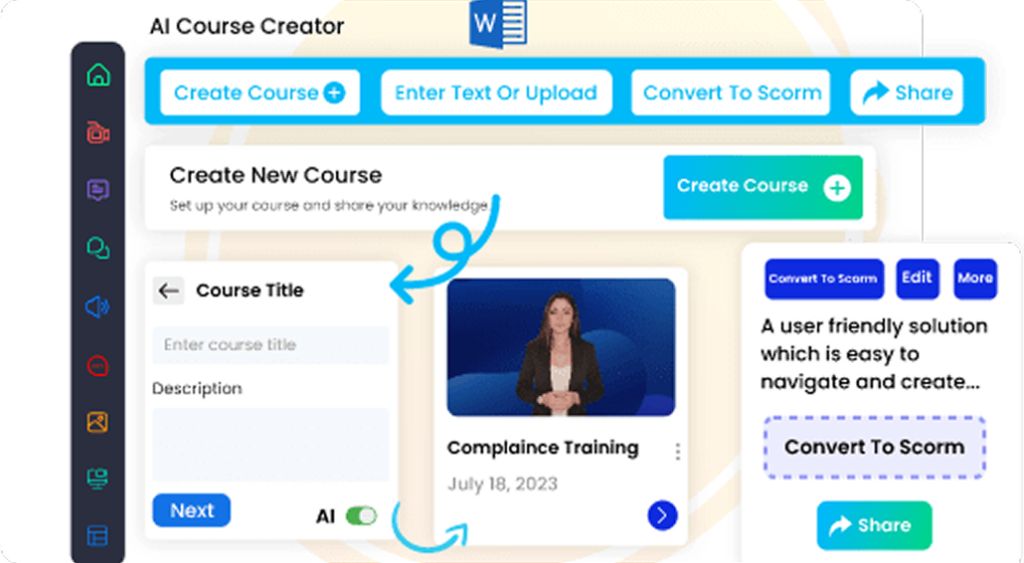
Organizations can easily customize training modules with CogniSpark’s built-in authoring tool, ensuring the content reflects current threats, internal IT policies, and regulatory requirements. Seamless integration with any LMS also allows for centralized progress tracking and audit-readiness.
Whether you’re onboarding new hires or upskilling existing staff, CogniSpark AI transforms your information security training into an engaging, compliance-ready initiative that empowers employees to be your first line of cyber defense.
Conclusion: Protecting Digital Assets Through Information Security Training
As the digital landscape continues to evolve, so too must the strategies for protecting valuable digital assets. Information security training for employees is one of the most effective ways to ensure your organization is equipped to prevent, detect, and respond to potential threats. By investing in security awareness training, companies can significantly reduce the risk of costly data breaches, comply with industry regulations, and foster a culture of cybersecurity that enhances overall business success.
The key takeaway is simple: investing in your employees’ security knowledge is investing in your company’s future. Whether you are just starting to implement security awareness training or looking to refine your current program, make sure to prioritize ongoing education to stay one step ahead of the threats that target your digital assets.
Access 100+ fully editable, SCORM-compatible courses featuring an integrated AI Tutor and an in-built authoring tool. Seamlessly compatible with any LMS, these courses are designed to elevate your training programs.
Explore Our eLearning Course Catalog